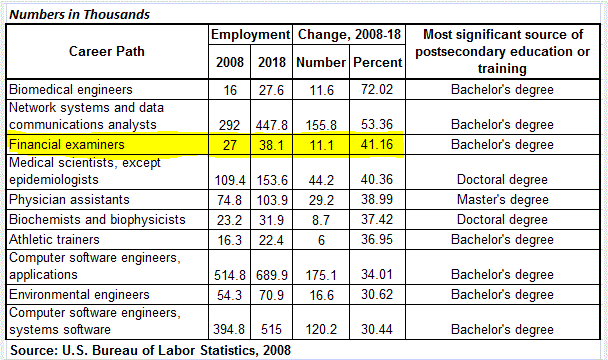
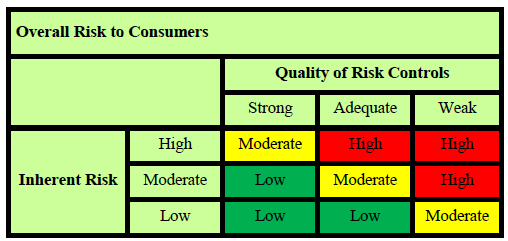
(NOTE: Although the vendor in question has been publicized by the NCUA, I will not name it here because it is not relevant. If you currently contract with the vendor you know who it is, and you need to know how to respond to the letter. If you don’t, you’ll need to know how to respond in case it happens to a critical vendor of yours at some point.)
What if you received this letter from the FDIC on one of your most critical service providers (summarized and redacted)?
“Dear Board of Directors,
Enclosed is a copy of the Information Technology (IT) Supervisory Letter based on the interim review of (your vendor). We are sending you this Supervisory Letter for your evaluation and consideration in managing your vendor relationship…I encourage you to review the Supervisory Letter as it discusses some regulatory concerns that require corrective action by (your vendors’) management and Board of Directors.
Sincerely,
FDIC Regional Director”
The letter states in part:
“(Vendors’) Executive Management supervision and control over the Risk Management (RM) and Information Security (IS) functions are unsatisfactory. Additionally, the Board of Directors (BOD) does not provide sufficient direction and oversight for management responsibilities, as well as for independent review in these areas by Internal Audit (IA). The breadth and severity of weaknesses noted at this IR stem from management’s failure to adequately address previously identified systemic issues and to take proactive measures to mitigate the identified systemic risks. These weaknesses had exposed serviced financial institutions to increased risk, and have raised concerns regarding management’s ability to establish and enforce effective information security measures commensurate with the needs of (vendor).”
So the FDIC conducted an IT Examination on the service provider. Nothing new there…IT service providers are subject to the same regulatory oversight as financial institutions, and even have their own Examination Handbook*. However, in this case the exam uncovered significant material weaknesses in their audit, management and IT controls. Weaknesses so severe that the FDIC felt it necessary to proactively notify all institutions under their regulatory responsibility that utilize the provider.
Since the FDIC stated that they are sending the letter for “your evaluation and consideration“, they clearly expect you to take specific action on this matter. Don’t be surprised to see them asking for your formal response during your next visit from them. So here is what you’ll need to do:
- The first thing you’ll want to do is call a meeting with the group you use to manage your vendor relationships. If you haven’t assigned vendor management responsibility to a management committee (as opposed to an individual), do so. IT Steering or Audit is a logical choice. Formally document in the committee that “the examiner’s letter represents certain concerns that will cause us to reevaluate the vendor, reassess the residual risk, and consider implementing additional compensating controls”.
- Request, review and evaluate the vendor’s response to the examiners letter. Determine whether the response is sufficient to address your concerns. If not, consider implementing the following additional compensating controls:
- Accelerate the normal annual due diligence process by requesting more frequent financial statements (quarterly instead of annual).
- Request that vendor provide additional 3rd party security reviews other than SSAE 16 if possible (i.e. SOC 2, PEN tests, etc.). The SOC 2 is a good choice, as it directly addresses controls related to privacy, security, confidentiality, integrity and availability…all the things that are important to you.
- Have legal review existing vendor contracts for possible breach of contract claims.
- Consider adding a “right to audit” clause in future contracts.
- Become active (or more active) in vendor user groups. The intent is to stay close to the situation, and possibly influence them to release additional 3rd party reviews (such as SOC 2).
It is important to take action even if you are in a long term contract with the vendor, or if the vendor would be difficult to replace. And you can’t take the position that since you can’t control what the vendor does, you’ll simply have to go along…that it’s not your problem to solve. Guidance makes it clear that “institutions should ensure the service provider’s physical and data security standards meet or exceed standards required by the institution.” So for all intents and purposes, the vendor’s deficiencies are your problem.
*According to the FFIEC:
The federal financial regulators have the statutory authority to supervise all of the activities and records of the financial institution whether performed or maintained by the institution or by a third party on or off of the premises of the financial institution.
The decision to examine a service provider is at least partially based on the number of Bank Service Company Act (BSCA) filings the regulators receive on the provider. I explain this here, and make the point that because the definition of a “Service Company” has expanded, more service providers can expect more examinations in the future.