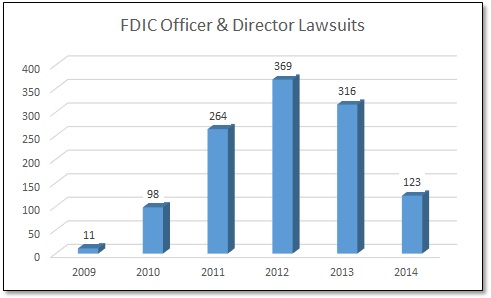
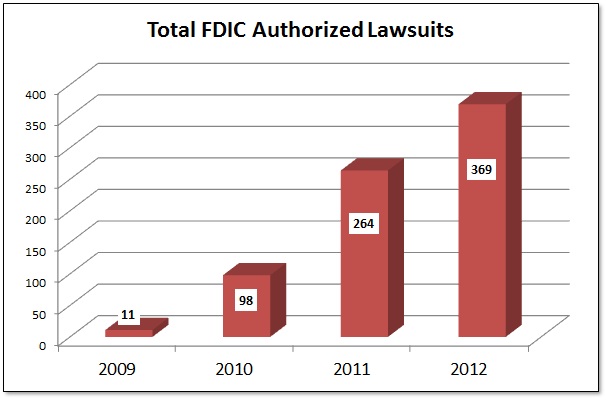
Unlike the PATCO ruling, a district court in Missouri has ruled in favor of the bank in an account takeover case brought by one of its commercial customers. This case was very similar to the PATCO case with one important exception, which I’ll discuss shortly. But it also raises some interesting questions that could impact financial institutions.
First, the details. In March 2010, BancorpSouth received a request via the Internet to execute a wire transfer in the amount of $440,000 on behalf of its customer, Choice Escrow and Land Title. The Bank wired the funds, and the following day the customer contacted the Bank to notify them that they they in fact did not authorize the wire transfer. The company filed suit to recover the loss, claiming that the Bank did not use appropriate security measures. But their claim wasn’t that appropriate security wasn’t made available, but that there were several security options available and the Bank allowed the customer to select an inferior option. This is quite different from the PATCO case, where strong authentication was available to the Bank from the software vendor, but the Bank in that case decided not to offer it to their customer. In this case the Bank offered both single and dual-control authentication options, and the customer waived the dual-control option. This gave any authorized user of the software the ability to initiate and approve a wire without requiring a second user to approve and release the funds. Using malware, a hacker was able to gain control of the PC, record the user name and password via a keystroke logger, and send the fraudulent wire.
The PATCO case was decided in favor of the customer because the Bank failed to make strong, commercially reasonable, authentication options available to the customer even though the software vendor offered them to the Bank. But in this case, the judge decided just the opposite; stronger options were made available, but were declined by the customer. Remember, according to UCC 4A the risk of loss for an unauthorized transaction will lie with a customer if the bank can establish that its security procedure is a commercially reasonable method of providing security against unauthorized payment orders. So, advantage Bank. But again, the customer claimed that the Bank should NOT have offered the weaker option to them knowing that it was insufficient to address the risks. In other words, simply offering the weaker option to the customer was an implicit acknowledgement by the Bank that it was commercial reasonable. In the end this argument was rejected because the Bank had documentation that it offered, and the customer refused, the stronger option multiple times.
Although this case turned out OK for the Bank, the verdict does raise several questions for financial institutions:
- Knowing that one option is better than another, should institutions even offer more than one authentication option to their customers? And what happens when a customer (or product) increases in risk? Do you require the users to upgrade?
- Since the judge in both this case and the PATCO case referenced UCC 4A as the legal basis for their decisions, should the FFIEC be more prescriptive about exactly what constitutes “commercially reasonable” (and what doesn’t)? The 2003 FFIEC E-Banking guidance says that “whether a method is a commercially reasonable system depends on an evaluation of the circumstances.” But the updated 2011 FFIEC authentication guidance doesn’t mention “commercially reasonable” (or UCC 4A) at all. Why not? Specifically, why not include the “…the risk of loss for an unauthorized transaction will lie with a customer if…” language?
- Are institutions putting too much faith in technical measures, and avoiding simpler, but more effective, controls? Anomaly detection is getting a lot of attention these days, but in this case Choice had a history of transfers with similar size and quantity, and anomaly triggers were not activated. Simple dual-authentication would have prevented this fraudulent transfer.
- On the other hand, are vendors overlooking more effective technologies, such as out-of-band authentication and secure DNS?
In summary, there are still questions, but there are also a couple of lessons financial institutions should take away from this. First, the court determined that although dual-control was more labor intensive for the customer, it was also the more secure option, and as such Choice should have opted for increased security over the increased inconvenience. Lesson? Perhaps you should be less concerned about inconveniencing your customers with increased security requirements, and more focused on convincing (i.e. educating) them on why a little increased effort on their part is justified…i.e. security trumps useability. Second, customer awareness efforts and documentation made all the difference in this case. If the Bank had not made, and documented, multiple efforts to implement stronger authentication, this case could easily have gone the other way.