The FBI, in association with the Financial Services Information Sharing and Analysis Center (FS-ISAC) and the Internet Crime Complaint Center (IC3), recently issued a fraud alert warning that criminals are using a multi-vector attack to compromise financial institution networks and initiate fraudulent wire transfers. The first thing that struck me about this attack is that although all the recent focus has been on strengthening controls on the merchant side, this is targeted not at the merchant, but directly at the financial institution itself.
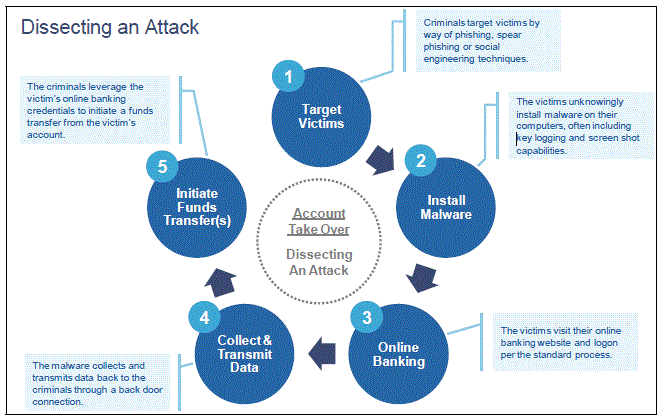
Simply put, the attack uses a combination of SPAM and phishing emails (#1 below), keystroke loggers, and remote access software (#2 below) to capture employee authentication credentials. A successful attack results in the employee’s PC being under the control of the criminal, who will then use the employee’s authority to initiate wires, approve them, and even override built-in transaction limits. The following graphic describes how the attack occurs, with the exception that in #5 the victim is the financial institution, not the on-line banking customer:
(Click here for original document)
It is important to understand that this is not a “proof-of-concept” attack, this is actually occurring, and has resulted in attempted transfers ranging from $400,000 and $900,000.
One of the unique indicators of the attack is that either just prior to or just after the attack, the institution’s website is targeted by a denial of service attack which is designed to slow or deny access to the FI’s website, distracting institution employees and preventing or delaying them from detecting the fraudulent transactions. They recommend that institutions monitor for spikes in website traffic that may indicate the beginning of the attack.
The alert also lists 17 best practice recommendations for financial institutions designed to prevent and detect this (and similar) attacks. It is not surprising that the first 5 recommendations address the weakest link; the employee. I previously identified the employee as the biggest single risk to information security, and employee training as a trend for 2012. Many of the other recommendations should be familiar to most FI’s; restrict user access rights and login times, review Anti-malware and Anti-virus defenses, implement anomaly detection, and utilize IPS and “white-lists” to prevent connections to suspicious sites. They also recommend that institutions strongly consider (their words, my emphasis) implementing out-of-band authentication for wire authorization. This is where the final authentication approval is send back to the originator via a communication channel other than the one used to initiate the transaction. This was also one of the recommendations from the FFIEC in their authentication supplement released last year.
In my opinion there are 2 controls financial institutions can implement now that will do more than any other to significantly reduce the incidence of fraudulent transactions. The first is out-of-band authentication, and the other is utilizing a secure DNS service, similar to this.