Background
In July of 2021, the three primary bank regulators (OCC, FDIC, and Federal Reserve) proposed new guidance on third-party risk management (TPRM). According to the agencies, “The proposed guidance provides a framework based on sound risk management principles that banking organizations may use to address the risks associated with third-party relationships.” In June of 2023 all three (OCC, FDIC, Federal Reserve) jointly adopted the final guidance, stating that: “The final guidance offers the agencies’ views on sound risk management principles for banking organizations when developing and implementing risk management practices for all stages in the life cycle of third-party relationships.” The agencies issued this simultaneously to “promote consistency in supervisory approaches”, something we fully support and have long advocated. It replaces each agency’s existing guidance on this topic and is applicable to all banking organizations supervised by the agencies (currently all financial institutions except credit unions).
Analysis
Since third-party relationships represent a significant amount of residual enterprise-wide strategic, operational, and information security risk to many financial institutions (we refer to this as the ‘inherited risk’), and because we believe regulators will greatly increase their scrutiny of your risk management efforts in this area, we’ve taken the last couple months to take a deep dive into the details of the guidance, and the potential implications to your TPRM program. The following is a summary of our observations.
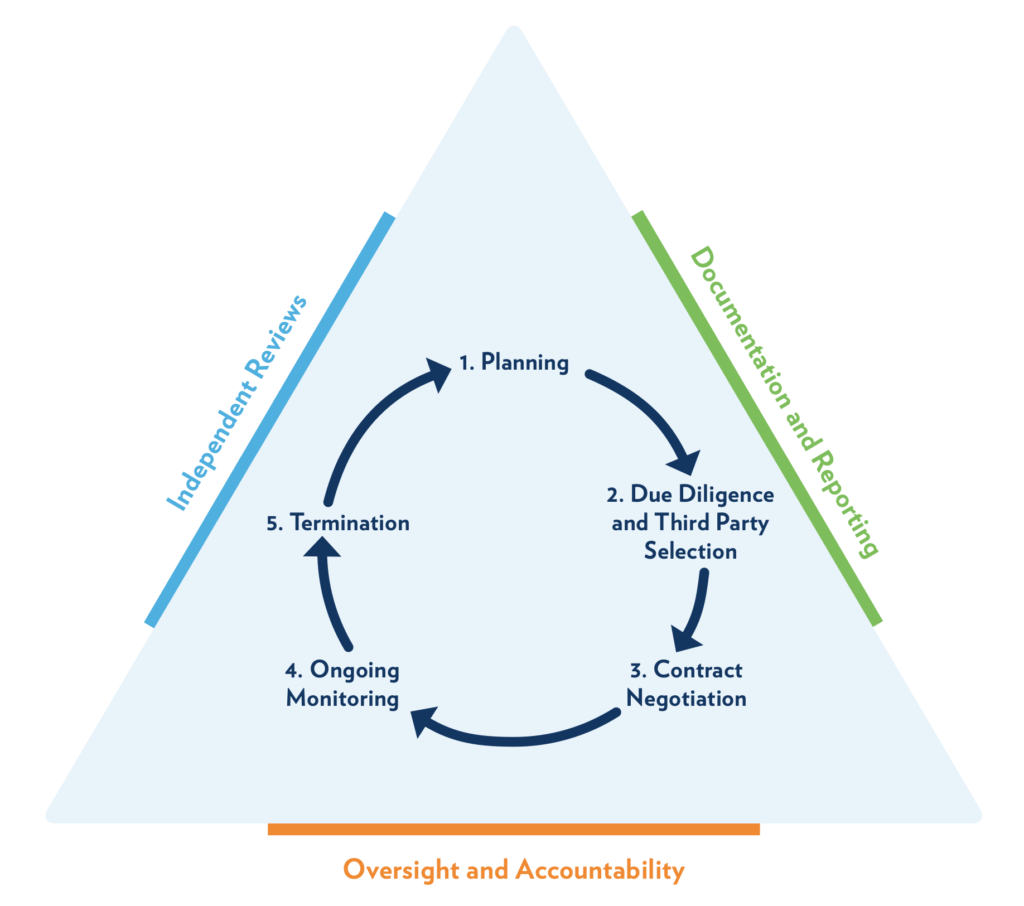
The agencies are advising a 5-step continuous life-cycle, wrapped in a formal, 3-phase governance process:
Each of the 5 phases consists of one or more sections, each of those with one or more statements:
- Planning – 1 section, 11 statements
- Due Diligence & Third-Party Selection – 14 sections, 40 statements
- Contract Negotiation – 17 sections, 61 statements
- Ongoing Monitoring – 1 section, 14 statements
- Termination – 1 section, 6 statements
and
- Governance – 3 sections, 29 statements
In total, there are 161 statements to evaluate, and they range from what we’ve interpreted as strong recommendations (“It is important for contracts to stipulate…”), to what we’ve determined are general observations and best practices (“May want to consider whether the contract…”).
Implications
In addition to factoring the “must have vs. nice to have” interpretation of each statement into the analysis, institutions will also need to determine the applicability of each individual statement to your organization. No fewer than 13 times in the guidance they mention some variation of “…commensurate with the banking organization’s risk appetite and the level of risk and complexity of its third-party relationships.” This is the applicability filter through which your “implement/do not implement” determination will pass. Simply put, although you should be familiar with each statement and its implications, you may not necessarily need to adopt them all. Indeed, if you currently have and maintain a compliant third-party management program, many are very likely already in place.
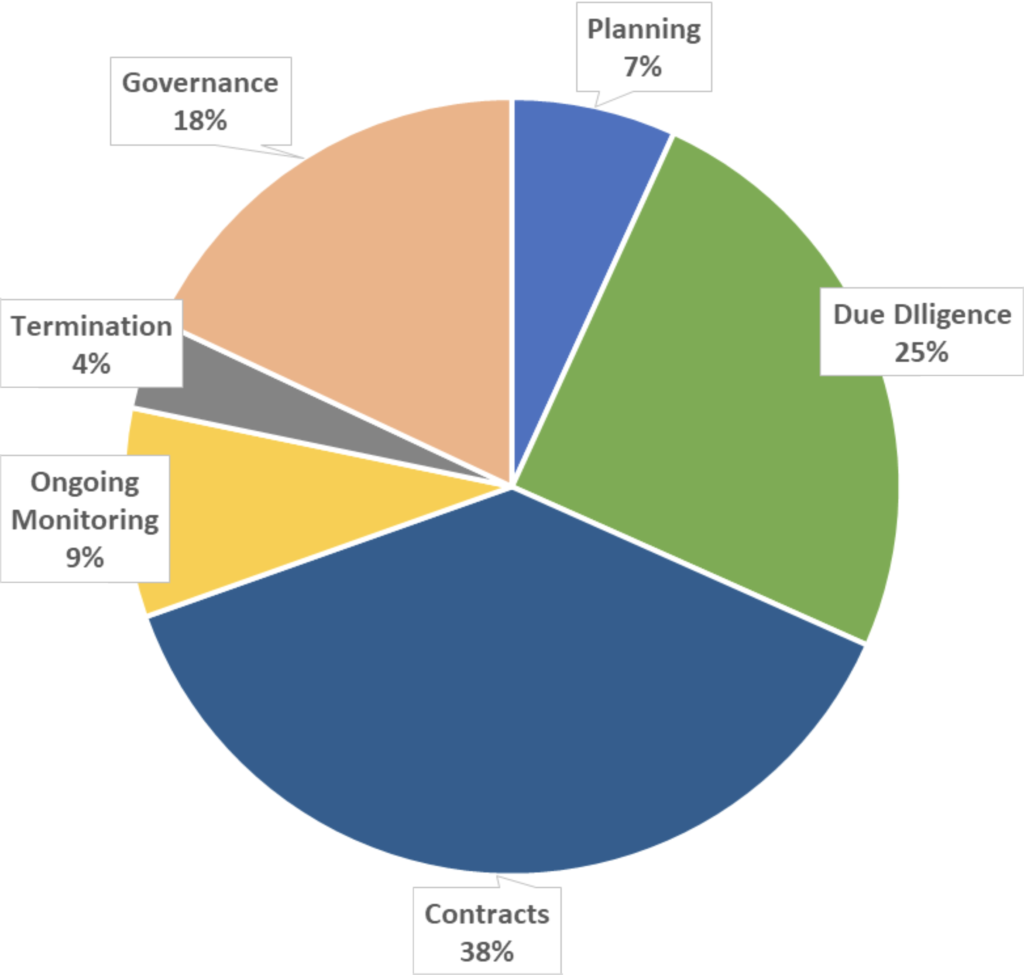
However, the single most important take-away for us is how the statements are distributed throughout the sections, which we believe give a pretty good indication of how the regulators will evaluate your TPRM program on the exam side. The vast majority (~70%) of statements are clustered in what can be referred to as “pre-engagement” phase, or before you formally engage (by contract or otherwise) with the third-party; the Planning, Due Diligence and Contract phases:
Does this mean that ~70% of your third-party management efforts going forward should be pre-engagement? We think that is a reasonable assumption, and we anticipate that sooner or later the regulators will also align their expectations in that direction. And since most compliant TPRM programs very likely already address the On-going Monitoring and Governance areas, the biggest challenge for most folks will be:
- Evaluating each of the 112 statements in this pre-engagement phase, and determining,
- Whether the statement is already addressed somewhere in your current program,
- If not, deciding whether or not to implement it given the criticality, complexity, and nature of the service(s) provided by the third-party given your risk appetite.
Pre-engagement vs. Pre-initiative
Although significantly expanded here, due diligence and contract considerations have, to a greater or lesser degree, always been in place. However, the biggest challenge for most institutions will be in the Planning phase. There are only 11 statements in this section, but they all address the risks of the business initiative itself, NOT the third-party! These statements include items such as:
- “Understanding the strategic purpose of the business arrangement…”
- “Identifying and assessing the benefits and the risks associated with the business arrangement…”, and
- “Considering the nature of the business arrangement…”
While most folks would consider these types of strategic (“why” instead of “how”) discussions to be beyond the scope of a traditional TPRM program, it is clear that regulators are certain to look for them going forward. Make sure to build this pre-initiative “why” phase into your program.
Summary
As with all things in the compliance space, be sure to document your entire decision-making process and don’t hesitate to reach out to our experts for assistance. As the guidance also states, “A banking organization may involve experts across disciplines, such as compliance, risk, or technology, as well as legal counsel, and may engage external support when helpful to supplement the qualifications and technical expertise of in-house staff.”
The agencies have indicated that they plan to develop additional resources to assist smaller, less-complex community banking organizations in managing relevant third-party risks, and we’re keeping an eye on this. In the meantime, we have created an interactive tool that lists all sections and statements, allows you to acknowledge each statement, add your notes, and track your overall progress. Click here for a copy.
We also offer a complimentary high-level regulatory compliance evaluation of your existing vendor management program. Click here to request more information.
We will be hosting an in-depth webinar and analysis on this new guidance on September 20th. A registration link will be available on our webinar page within the next week.