FFIEC Releases Cybersecurity Assessment Tool
UPDATE: Safe Systems just released their Enhanced CyberSecurity Assessment Toolkit (ECAT) – This enhanced version of the FFIEC toolkit addresses the biggest drawback of the tool; the ability to collect, summarize, and report your risk and control maturity levels.
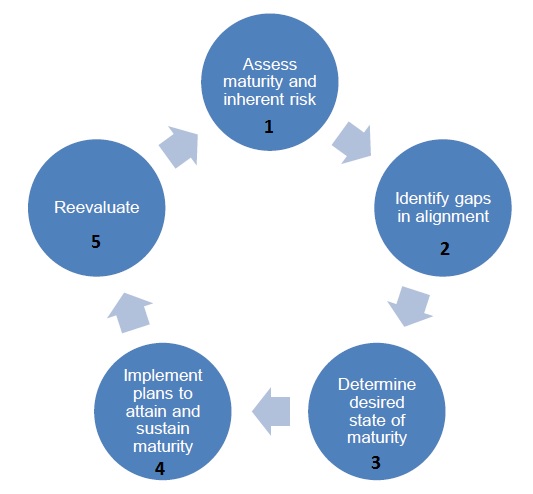
Once risks and controls have been assessed (Step 1 below), institutions will now be better able to identify gaps in their cyber risk program, which is step 2 in the 5 step process.
This long-anticipated release of the Cybersecurity Assessment Tool (CAT) is designed to assist institution management in both assessing their exposure to cyber risk, and then measuring the maturity level of their current cybersecurity controls. Users must digest 123 pages, and must provide one of five answers to a total of 69 questions in 10 categories or domains. This is not a trivial undertaking, and will require input from IT, HR, internal audit, and key third-parties.
After completing the assessment, management should gain a pretty good understanding of the gaps, or weaknesses, that may exist in their own cybersecurity program. As a result, “management can then decide what actions are needed either to affect the inherent risk profile or to achieve a desired state of maturity.” I found the CAT to be quite innovative in what it does, but it also has some baffling limitations that may pose challenges to many financial institutions, particularly smaller ones.
[pullquote]The CAT is quite innovative in what it does, but it also has some baffling limitations…[/pullquote]
First of all, I was stunned by the specificity of both the risk assessment and the maturity review. Never before have we seen this level of prescriptiveness and granularity from the FFIEC in how risks and controls should be categorized. For example, when assessing risk from third-parties:
- No third-parties with system access = Least Risk
- 1 – 5 third parties = Minimal Risk
- 6 – 10 third parties = Moderate Risk
- 11 – 25 third parties = Significant Risk, and
- > 25 third parties = Most Risk
Again, this is quite different from what the FFIEC has done previously. If Information Security guidance used the same level of detail, we might see specific risk levels for passwords of a certain length and complexity, and correspondingly higher control maturity levels for longer, more complex passwords. Of course we don’t see that from current guidance, what we get is a generic “controls must be appropriate to the size and complexity of the institution, and the nature and scope of its operations”, leaving the interpretation of exactly what that means to the institution, and to the examiner.
I see this new approach as a very good thing, because it removes all of the ambiguity from the process. As someone who has seen institutions of all sizes and complexities struggle with how to interpret and implement guidance, I hope this represents a new approach to all risk assessments and control reviews going forward. Imagine having a single worksheet for both institutions and examiners. Both sides agree that a certain number of network devices, or third-parties, or wire transfers, or RDC customers, or physical locations, constitute a very specific level of risk. Control maturity is assessed based on implementation of specific discrete elements. Removing the uncertainty and guess-work from examinations would be VERY good thing for over-burdened institutions and examiners alike.

7 Reasons Why Small Community Banks Should Outsource IT Network Management
So all that is good, but there are 2 big challenges with the tool; collection, and interpretation and analysis. The first is the most significant, and makes the tool almost useless in its current format. Institutions are expected to collect, and then interpret and analyze the data, but the tool doesn’t have that capability to do that because all the documents provided by the FFIEC are in PDF format.
If you can figure out how to record your responses, that still leaves the responsibility to conduct a “gap” analysis to the institution. In other words, now that you know where your biggest risks reside, how do you then align your controls with those risks?
One more challenge…regulators expect you to communicate the results to the Board and senior management, which is not really possible without some way of collecting and summarizing the data. They also recommend an independent evaluation of the results from your auditors, which also requires summary data.
In summary, there is a lot to like in this guidance and I hope we see more of this level of specificity going forward. But the tool should have the ability to (at a minimum) record responses, and ideally summarize the data at various points in time. In addition, most institutions will likely need assistance summarizing and analyzing the results, and addressing the gaps. But at least we now have a framework, and that is a good start.
4 comments
Write a Comment
You must be logged in to post a comment.




August 26, 2015
I was hoping for a tool that I could download and use locally rather than a website tool. I have a spreadsheet version that I can save and adjust if needed. I will probably stick with that one rather than answer all the questions again.
August 26, 2015
RJ, we considered adding an import function but it would add considerable time to the roll-out. Unfortunately there is no way to export the data from the FFIEC form either, so any tool would required a re-key of data. We’re still more than happy to help you with the gap analysis using your spreadsheet!
August 26, 2015
What would be the reason the reCAPTCHA box is not showing up for me to check on the enrollment screen? Thanks for the tool. I converted the FFIEC pdf into my spreadsheet, but the end result reporting was a tough one. I did use another tool, however, I would like to use this one too to compare results. You are correct the focus is different and takes thought to pull it together.
Thanks as always for being a great support to your customers!
August 26, 2015
Hi Donna, not sure why you’re having trouble with the reCAPTCHA. I don’t consider you a robot if that helps! You’re correct though, making sense of the results will be the next challenge.