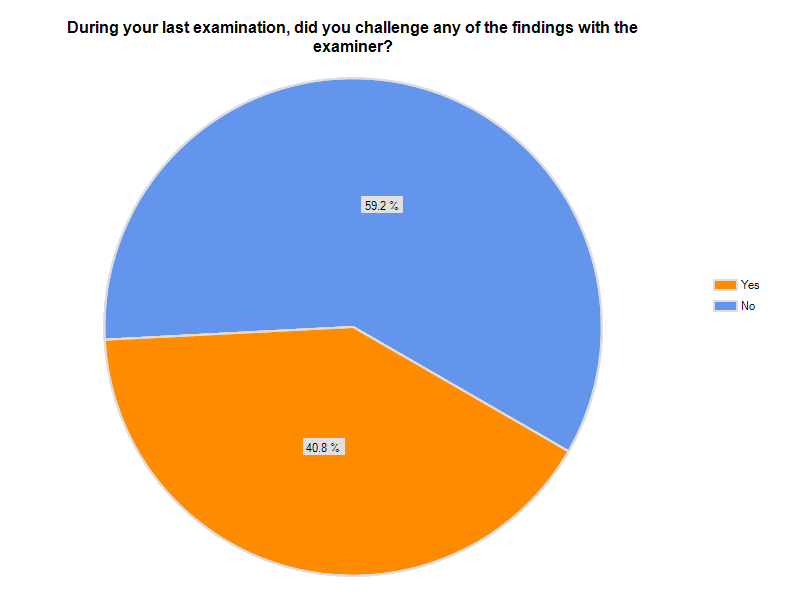
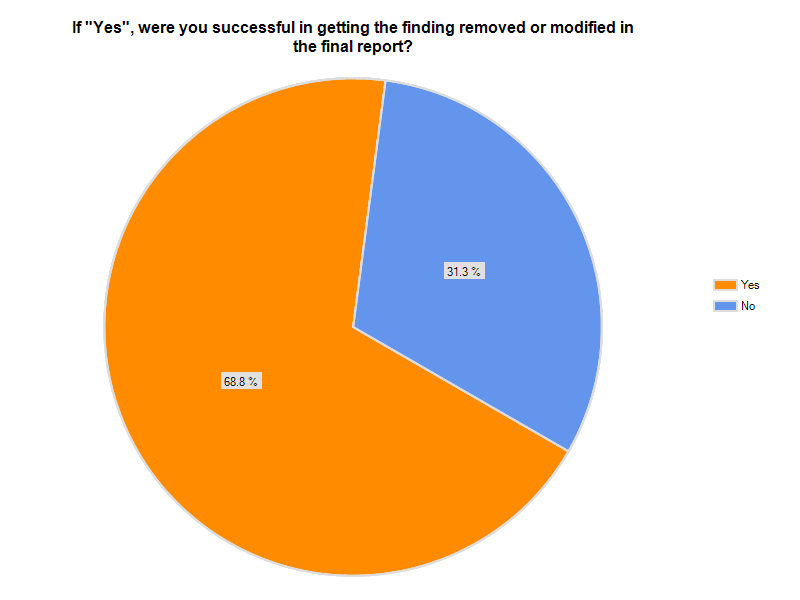
I asked in my previous post whether or not the regulators should share any of the blame when institutions fail, and if so, should they shoulder any of the liability? The thought occurred to me as I was reviewing some recent Material Loss Reviews.
A Material Loss Review (MLR) is a post-mortum written by the Office of Inspector General for each of the federal regulators with oversight responsibility after a failure of an institution if the loss to the deposit insurance fund is considered to be “material”. (The threshold for determining whether the loss is material was recently increased by the Dodd-Frank Act from $25 million to $200 million, so we are likely to see fewer of these MLR’s going forward.) All MLR’s have a similar structure. There is an executive summary in the front, followed by a break-down of capital and assets by type and concentration. But there is also a section that analyzes the regulator’s supervision of the financial institution, and I noticed a recurring theme in this section:
- …(regulator) failed to adequately assess or timely identify key risks…until it was too late.
- …(regulator) did not timely communicate key risks…
- …Regulator should have taken “a more conservative supervisory approach”, and used “forward-looking supervision”.
- …examiners identified key weaknesses…but…they did not act on opportunities to take earlier and more forceful supervisory action.
- …serious lapse in (regulator’s) supervision
- …(regulator), in its supervision…did not identify problems with the thrift
- …(regulator) should have acted more forcefully and sooner to address the unsafe and unsound practices
- …(regulator) did not fully comply with supervisory guidance
There were also many references to the responsibilities of the Board, which I addressed here, but in almost every case the regulator was found at least partially responsible for the failure of the institution.
Here is where you can find the reports for each regulator:
I encourage you to take a look at these and draw your own conclusions as to the issues of responsibility and liability. But clearly there are lessons to learn from any failure, and one lesson that I think we should all learn from this is that regulators will be pressured to be much more critical going forward. (I.e. quicker to apply “Prompt Corrective Action“.) After all, no one likes to be called out for doing a bad job.
One other part I found interesting (in the sense that it perfectly fits the narrative) is where the review lists all examination CAMELS ratings in the periods immediately prior to the failure. What struck me was how many times institutions scored 1’s and 2’s just prior to the failure, and then dropped immediately to 4’s and 5’s in a single examination cycle. Again, the lesson is that there will be tremendous downward pressure on CAMELS scores. And don’t think that just because you are healthy you’re immune from the additional scrutiny. As one MLR stated “…a forceful supervisory response is warranted, even in the presence of strong financial performance.”